Endpoint Security Checklist
Posted on July 20, 2022 by Fusion Connect
Endpoint Detection and Response (EDR) is a tool used to detect and contain security incidents, with remediation guidance. It can be managed or unmanaged. Managed Endpoint Security goes beyond the EDR tool to offer more comprehensive endpoint management that further reduces risk and ensures every endpoint is secure.
Both solutions have a common goal: Protect the thousands of endpoints that exist in typical mid-market and enterprise companies. Many organizations don’t even know how many endpoints exist in their environment, let alone how to secure them. Especially given the rise of remote work, endpoint security is a growing concern, and both EDR and Managed Endpoint Security can guard against ransomware, fileless malware, and other attacks. The difference is in their capabilities and extent of their scope.
EDR is a tool that lives on every device and acts like a personal firewall, providing anti-virus and zero-day threat protection. It’s an essential element of security, but doesn’t go as far as many enterprises need.
Managed Endpoint Security augments EDR with three major components:
visibility, control, and security.
- Visibility uncovers all the assets on an organization’s network and how they’re performing.
- Control allows you to push out software and firmware updates and better manage your entire ecosystem of endpoints.
- Security involves vulnerability scans and searching for devices out of compliance or that have security holes so you can prioritize which assets to fix first.
On top of that, EDR can be an unmanaged tool that an organization runs internally or a managed tool run for them by an MSP. Managed Endpoint Security is a managed service that multiplies your team’s efforts by keeping better track of your assets and the vulnerabilities that might threaten them.
The Top Five Considerations for Your Endpoint Security Checklist
There’s a lot to consider when you’re looking at endpoint security options. Which tools and services you choose will depend on your organization’s individual needs. But, there are some features that rise above the rest in importance and should be at the top of your list.
Here are the top five considerations your endpoint security checklist:
#5 – Asset discovery and inventory
To protect your endpoints, you need to know what endpoints you have, and what software they’re running. Strong endpoint security starts by identifying all devices across your cloud, on-premises, and remote environments as well as all software running on those devices and how it’s being used. Visibility not only helps IT monitor and remediate performance issues, but also understand how risky any given vulnerability is to your organization.
#4 – Centralized configuration and patch management
By centralizing management, you can configure, install, update, or remove software from any device automatically. As a result, you can increase the efficiency of your IT operations, ensure patching happens on time, and more easily meet compliance requirements.
#3 – Vulnerability scanning
Probe devices and applications for vulnerabilities and compliance exposure. Even across widely distributed infrastructure with thousands of devices, vulnerability scanning will report which endpoints need remediation within minutes, allowing you to quickly address any issues before they become bigger risks.
#2 – Real-time threat response
Minimize the impact of threats with automated hunting, early detection, and rapid investigation and remediation. Minimize business disruption by quickly snuffing out any threats.
#1 – Managed Endpoint Security
Hand off managing your endpoint security to a team of security veterans who will identify and monitor your endpoints, manage policies and updates, and investigate and respond to threats to keep your business running smoothly and safely.
Endpoint Security Checklists
Technologies and Resources
The endpoint security market is rife with point solutions. There are tools for tracking assets, tools for discovering what’s running on those assets, tools for patching those assets. You have to look across an array of tools to know what you have, whether those devices are up to date, and then actually fix any problems. Not to mention that having so many point solutions running on a single device will inevitably slow down the machine, and in many cases, the end users.
Consolidating these tools creates a seamless workflow that’s much easier to manage, doesn’t slow down endpoints, and delivers a higher level of security. You can patch large numbers of machines in minutes as opposed to days or weeks.
By using a single tool with multiple functions, you can make more efficient use of network connectivity. If you need to quickly find out how many endpoints are running software with a vulnerability, you might consult a database. This is is quick, but the information is likely out of date or difficult to maintain.
Alternatively, you might have multiple tools that can provide up to date information, but might take a while to gather it and put extra strain on the network. A consolidated tool gives you a quick and accurate assessment without being an excessive drain on connectivity.
Increasingly, endpoint security tools are using AI, instead of signatures, to identify and block known and unknown malware. When a tool relies solely on signatures, it’s not only time consuming and a burden on the network, it can only ever catch known malware. AI offers more sophisticated protection. It identifies anomalies whether they’re known or not, without taxing the network.
Do You Have an In-house Endpoint Security Checklist?
We asked 100 IT Professionals: Do you have an Endpoint Security Checklist?
The results point to a glaring gap in security at many of the organizations surveyed. Not even half have a security checklist in place. This potentially leaves an open door for a vulnerability that could hit an asset the organization didn’t even know it had.
Do you have an Endpoint Security Checklist?
No, Outsource All 20%
Yes, Love Security Checklist 73%
No, but we need one – 7%
It’s concerning that so many organizations lack an endpoint security checklist. This is the 7% cyber threats and hackers will look for. Perhaps the rush to remote work during the pandemic left them unprepared or added new remote devices to their list of endpoints they need to manage. Perhaps they’ve simply focused their time, attention, and budget elsewhere. No matter the reason, it’s time to renew a focus on endpoint security.
No, we outsource everything – 20%
The number of organizations that outsource their endpoint security checklist is a relatively small portion of the group, but potentially the best protected. By putting their endpoint security in the hands of a managed service provider, these organizations not only have a team dedicated to their endpoint security, but free their security and IT teams to focus on other areas of the business.
Yes, we love a security checklist – 73%
Three quarters of organizations surveyed prefer to handle their endpoint security checklist themselves. When we speak to businesses that create, manage, and act on their in-house security checklists, we hear common themes: decisions are mostly down to budgets, speed of delivery, and the trust they hold for current suppliers. It can certainly be time and resource intensive to manage in-house. But, they need the task completed effectively. Given the tight (and expensive) market for talent, this has become a harder practice. Especially for an enterprise trying to build a best-in-class security program.
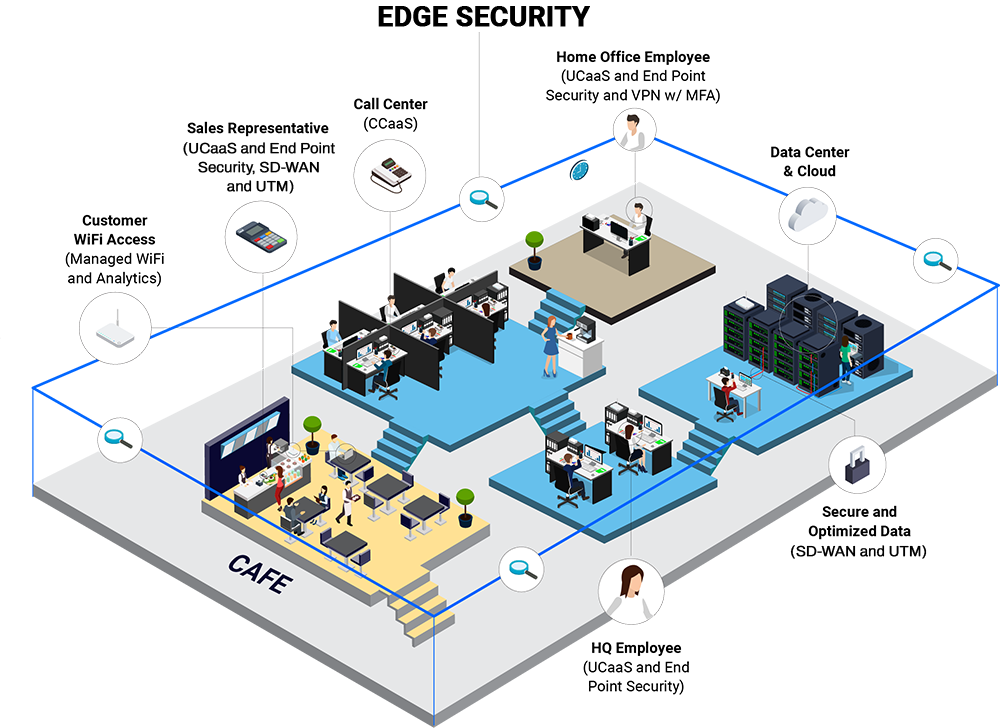
Endpoint Management and Security for an Enterprise Business
Some 76% of IT security decision-makers said use of endpoint devices increased in their organization since the start of the pandemic. Only 58% could identify every vulnerable asset within 24 hours of a critical exploit. They know there’s an issue. Some 84% of IT operations teams said there was significant room for improvement in their ability to manage endpoints. And the need is urgent. The average cost of a successful endpoint attack [PDF] is $8.94 million.
Endpoint management and security not only helps mid-market and enterprise companies get a handle on all the endpoints connecting to their systems, but also keep up as the environment changes. For the many organizations that aren’t certain how many or what devices are part of their environment, endpoint management allows them to discover and keep tabs on each one and the software it’s running so that if a vulnerability is ever discovered, the proper devices can be efficiently patched.
That patching and other maintenance is all the easier with endpoint management and security, which centralizes the application of patches, software updates, configurations, and other policy changes to ensure every endpoint on your network is up to date.
Most importantly, endpoint management and security automates scanning for vulnerabilities and proper compliance. Once detected, vulnerabilities can be efficiently mitigated to avoid a costly and time-consuming disruption.
Your Endpoint Security Checklist
The Conclusion
Every mid-market and enterprise company should be working on or updating their endpoint security checklist. It’s a common blind spot for many, and one that can prove costly in the event of an attack.
Even companies that have been working on the problem find themselves with a hodgepodge of point solutions that slow and complicate the work of endpoint security and management.
As part of a successful endpoint management and security checklist, be sure to cover the three main areas of visibility, control, and security, all three of which work together efficiently to discover devices in your environment, manage them from a single screen, and ensure software and firmware are up to date, enabling the swift patching of any vulnerabilities discovered.
It’s important to evaluate the capabilities of the technology of course, but also the resources you’ll need to effectively manage your endpoint security program. Turning to a managed endpoint and security provider augments your team with the latest technology and security experts who keep your environment up to date, secure, and compliant.
Managed endpoint and security consolidates the many practices on any endpoint security checklist under a single umbrella so they’re more efficient to manage and offer more comprehensive and thorough security. Whichever path you choose, updating or assembling an endpoint security checklist for your organization can keep you on track to discover the devices in your environment, keep them current, and fend off any attacks.
Why a Managed Service provider (MSP) would also have a standalone MSSP and Endpoint Security offering
Managed service providers (MSPs) have an MSSP or endpoint security offering to specialize in security. The term “managed service” is a blank slate that can apply to a number of services, with security being one of the most crucial for any organization. The MSSP and endpoint specialization ensures the MSP has the talent, the technology, and the experience to offer organizations a world-class security team far faster and for a far lower budget than building one in house.